ISO 27001 – Where to Start?
Recommended by
 Dejan Kosutic
Dejan Kosutic
 Dejan Kosutic
Dejan Kosutic
Best Articles to Start With

Articles
ISO 27001
What is ISO 27001? Quick and Easy Explanation.
by Dejan Kosutic
Best Tools to Implement and Learn
Conformio ISO 27001 software
Simplifies ISO 27001 certification effort by guiding you through implementation steps and creating documentation automatically.
ISO 27001 Documentation Toolkits
All of the key ISO 27001 documents, records, and templates necessary to complete your certification process.
ISO 27001 Trainings
World’s most popular ISO 27001 courses for beginners, and for experienced professionals.
Implementation
view all
AI Tools
AI-Powered
Tools
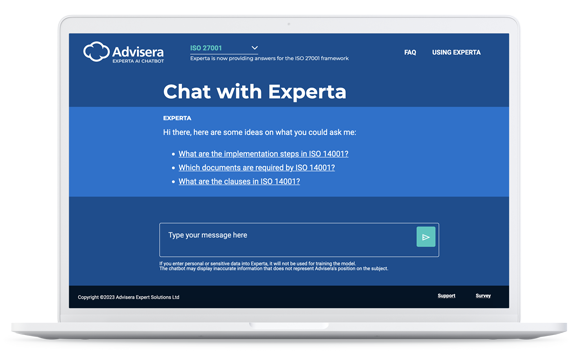
Experta: AI-Powered ISO Knowledge Base
Most accurate chatbot trained with Advisera’s proprietary ISO 27001 knowledge base.
Try Now
AI-powered
Regular Toolkits
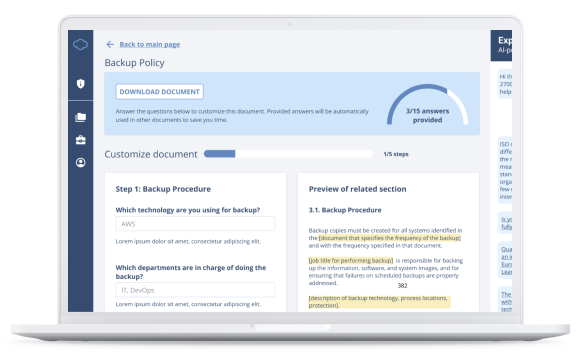
ISO 27001 Documentation Toolkit
Save money and speed up your ISO 27001 implementation process with AI automated document generation software.
Learn more
Documentation
view all
Certification
Training
view all
Risk Management
Internal audit
Roles & responsibilities
view all
Tools
view all
Related standards
view all
IT security controls
view all
Industries
General
view all



